Are you still using the default “Administrator” account to manage Windows devices in your corporate environment? Does those passwords for the default “Administrator” account are pre-defined and managed locally with on a regular basis? If the answer is for sure, then you should implement LAPS as a better solution.
What exactly is LAPS?
LAPS stands for Local Administrator Password Solution is a Windows feature that automatically manages and backs up the password of a local administrator account on your Azure AD joined devices or Windows Server AD Joined devices. During the past few years, you may only deploy LAPS to Active Directory (on premises) joined device with Windows Server required, and the whole process were tedious… This kind of implementation was called the legacy solution or legacy LAPS. As on Apr 2023 Microsoft announced new way to implement LAPS for Azure AD joined device with Intune this implementation is called Windows LAPS. You can also use Windows LAPS to automatically manage and back up the Directory Service Restore Mode (DSRM) account password on your Windows Server Active Directory domain controllers.
By leverage LAPS, you can regularly rotate the local administrator account password to improve security for help desk scenarios; and protect against pass-the-hash and lateral-traversal attacks; Ability to retrieve local administrator account password that are otherwise inaccessible.
When back up password to Azure Active Directory, managed local account passwords are stored on the Azure Active Directory device object. Data stored in Azure Active Directory is highly secure, but for extra protection, the password is further encrypted before it’s persisted. This extra encryption layer is removed before the password is returned to the authorized clients. The Windows LAPS password encryption feature is based on the Cryptography API: Next Generation Data Protection API. The underlying encryption is based on Advanced Encryption Standard 256-bit key (AES-256) encryption.
By default, only members of the Global Administrator, Cloud Device Administrator, and Intune Administrator roles can retrieve the clear-text password.
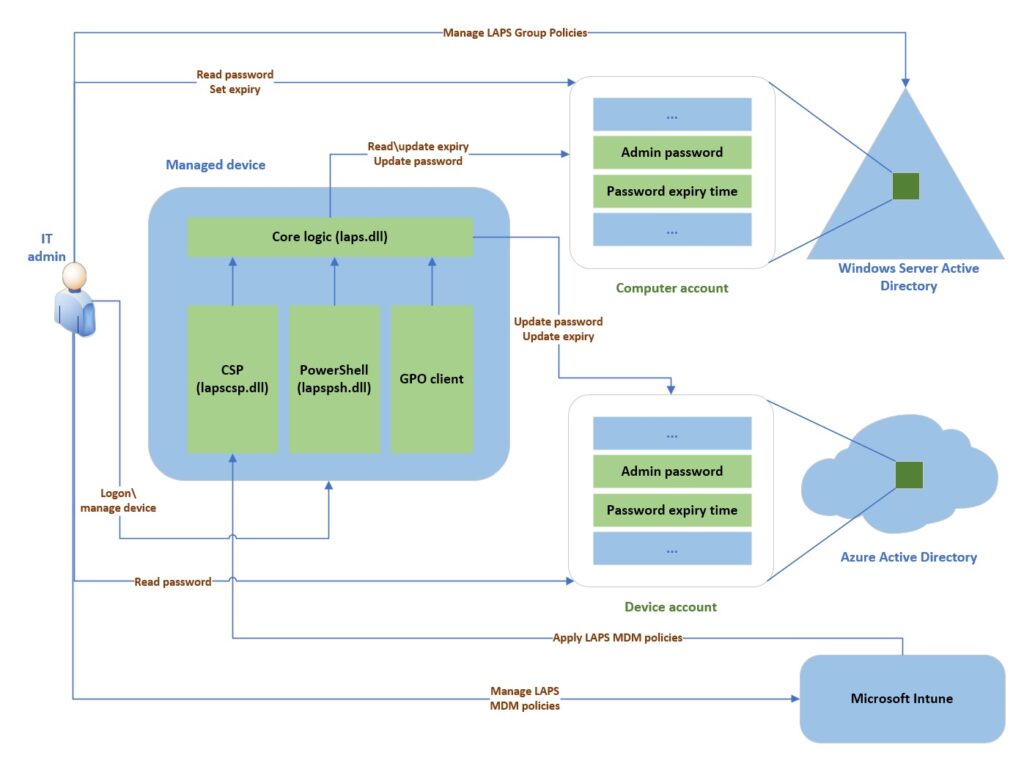
How to implement LAPS for Azure AD joined devices?
Before starting to implement LAPS in your organization for all Azure AD joined devices, make sure those targeted devices are meet the following prerequisites:
1.Supported Windows editions:
- Windows 10 Pro, EDU, and Enterprise
- Windows 11 Pro, EDU, and Enterprise
- Windows Server 2019
- Windows Server 2022 and Windows Server Core 2022
2.Installed April 11, 2023 security updates (KB5025239) and Cumulative updates.
After you checked above prerequisites are meet, then you may proceed the following steps to enable Windows LAPS with Azure AD.
1.Sign-in to Microsoft Entra admin center (https://entra.microsoft.com) or Azure Portal(https://portal.azure.com) with your account (must be assigned with Cloud Device Administrator / Global Administrator).
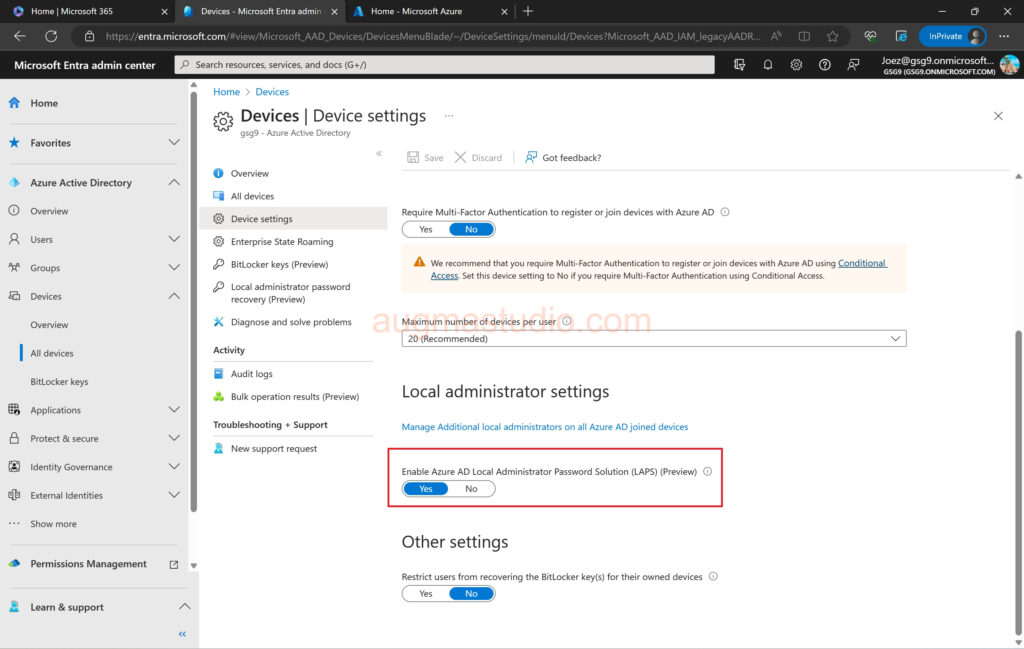
2.Navigate to Azure Active Directory > All devices > Device settings > select “Yes” under “Enable Azure AD Local Administrator Password Solution (LAPS) (Preview)”.
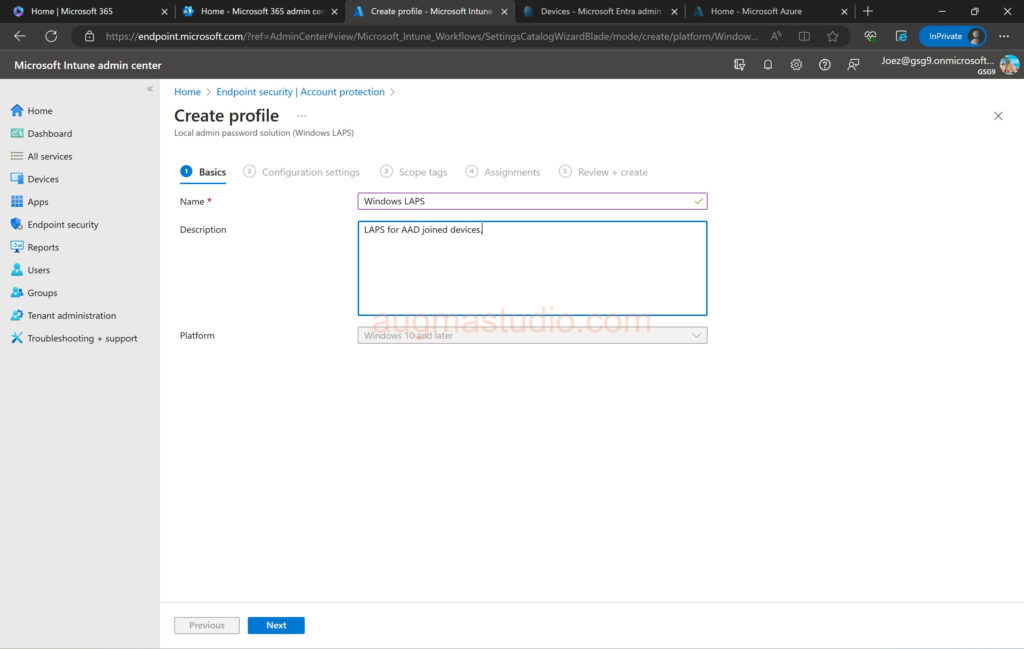
3.Configure a client-side policy and set the BackupDirectory to be Azure AD. As we implemented Windows LAPS for Azure AD joined devices, we need to create and assign policy from Intune. To follow best practices and reduce potential conflicts, we need to assign single LAPS policy to each device through device groups instead of user groups.
4.Sign-in to Microsoft Intune admin center (https://endpoint.microsoft.com) > Endpoint security > Account protection > Create Policy.

5.Select “Windows 10 and later” under Platform > select “Local admin password solution (Windows LAPS)” under Profile > click Create.

6.Naming the profile and add some descriptive words > click Next.
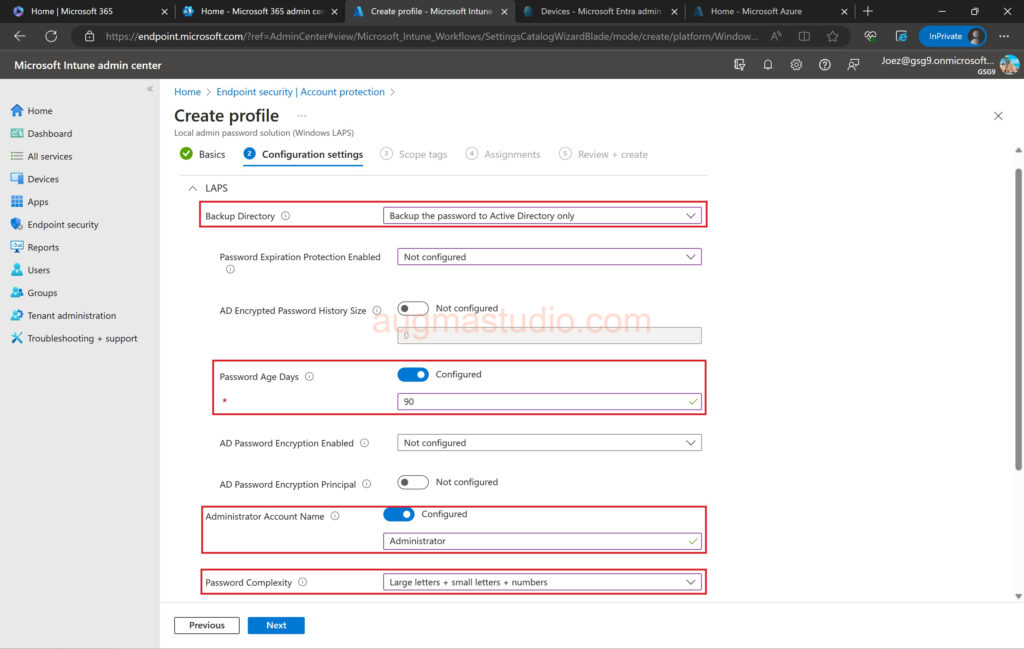
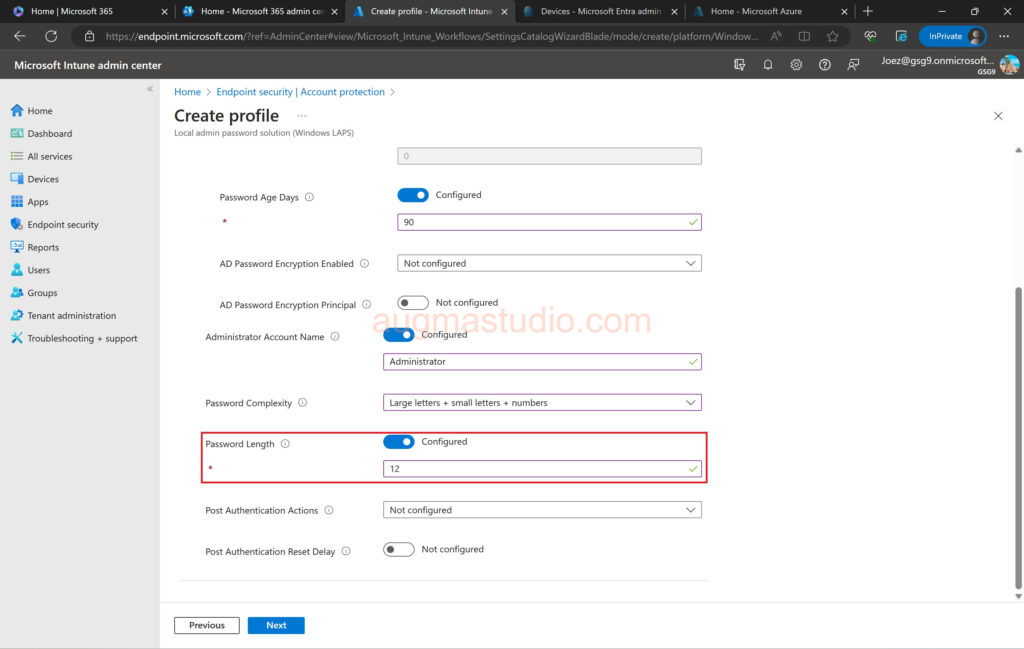
7.Setup the following options according to your demands > then click Next.
8.Adding Scope tags if required.
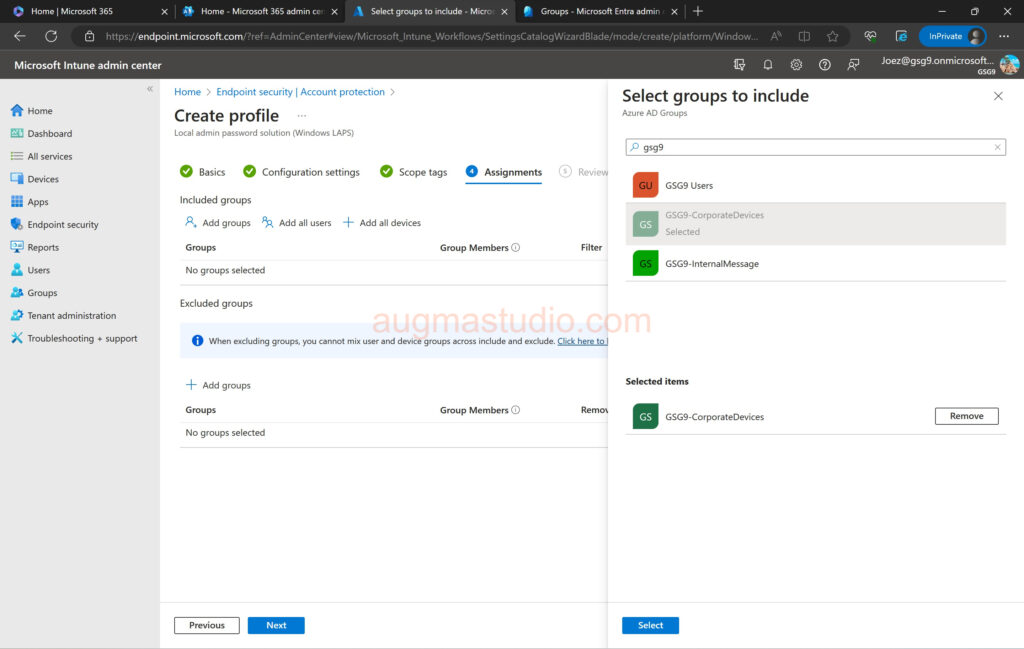
9.Assign the profile to desired group by click “Add groups” > select desired group > click Select > click Next. As mentioned above it is better to assign to device group instead of user group.
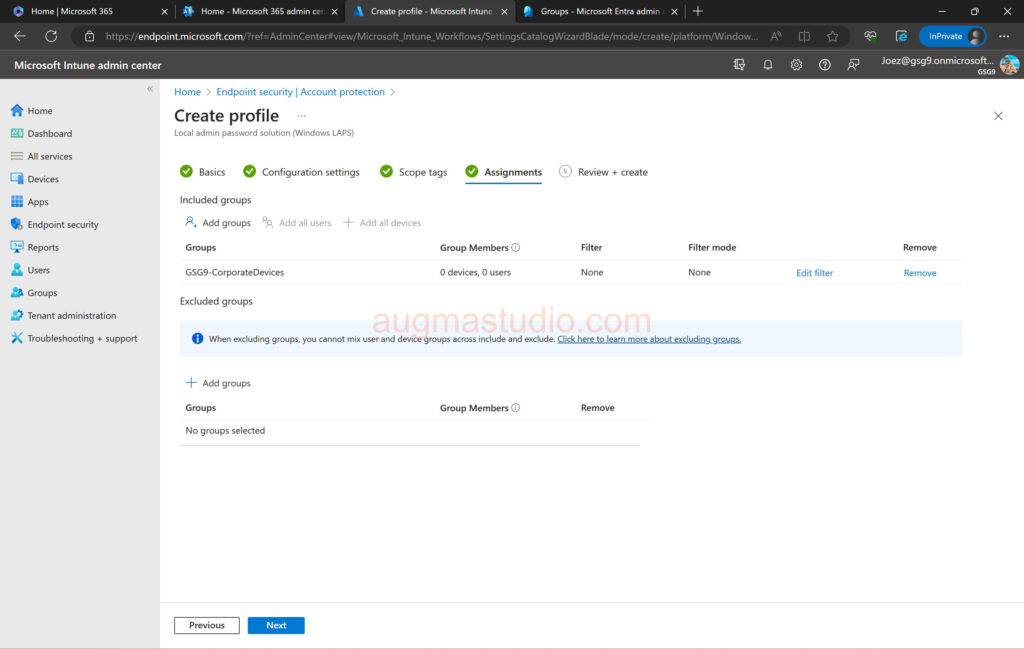
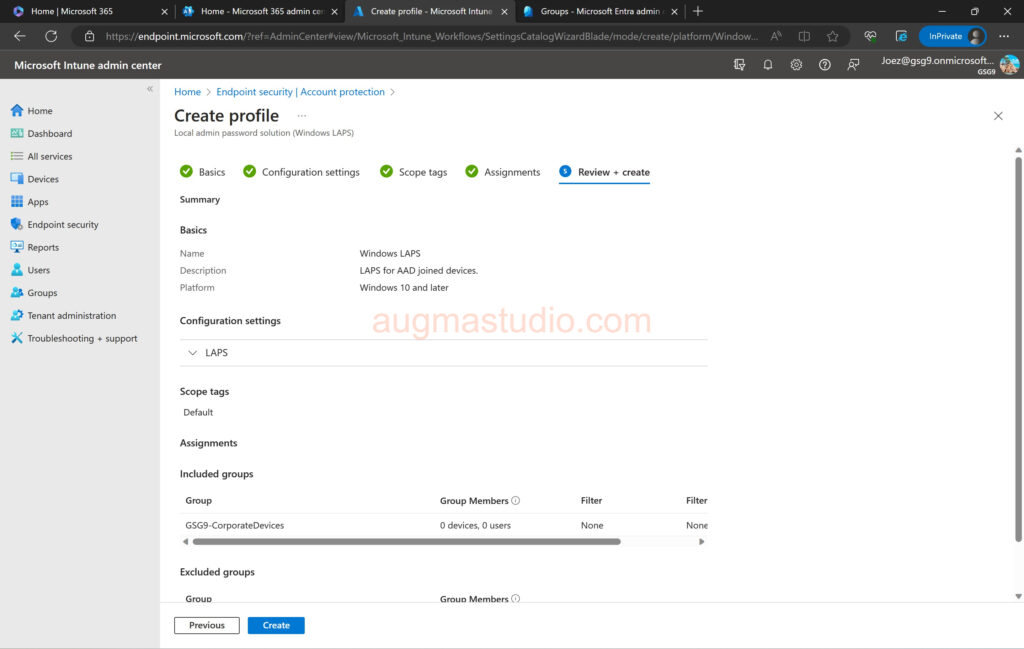
10. Review profile if all good then click Create.
How to retrieve the pw for targeted device?
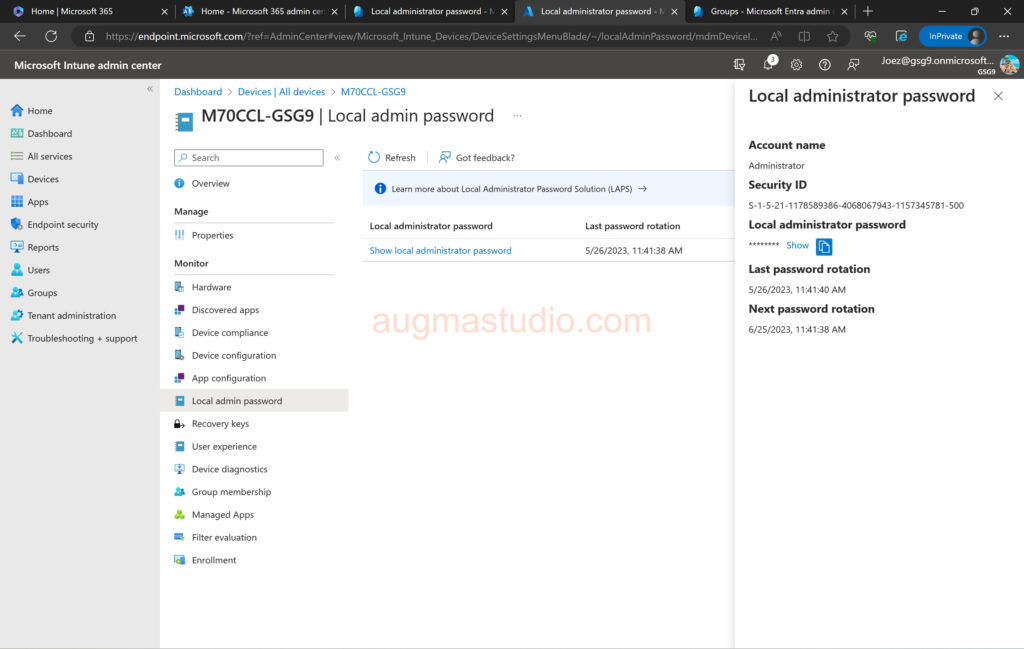
To retrieve password for the local administrator account you can operate via either Azure Portal or Intune admin center by follow below steps:
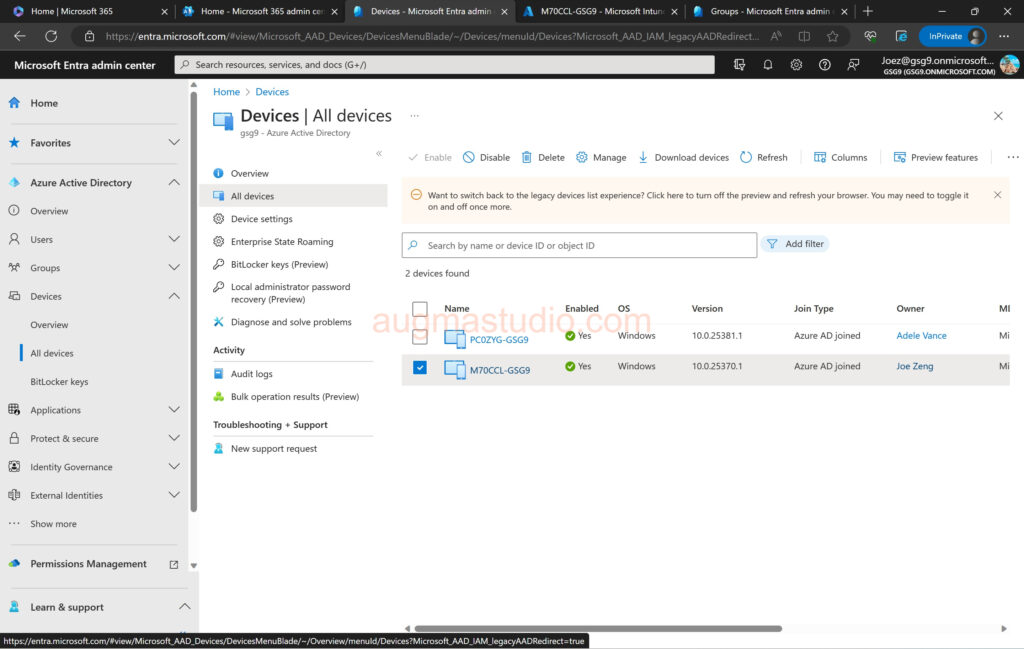
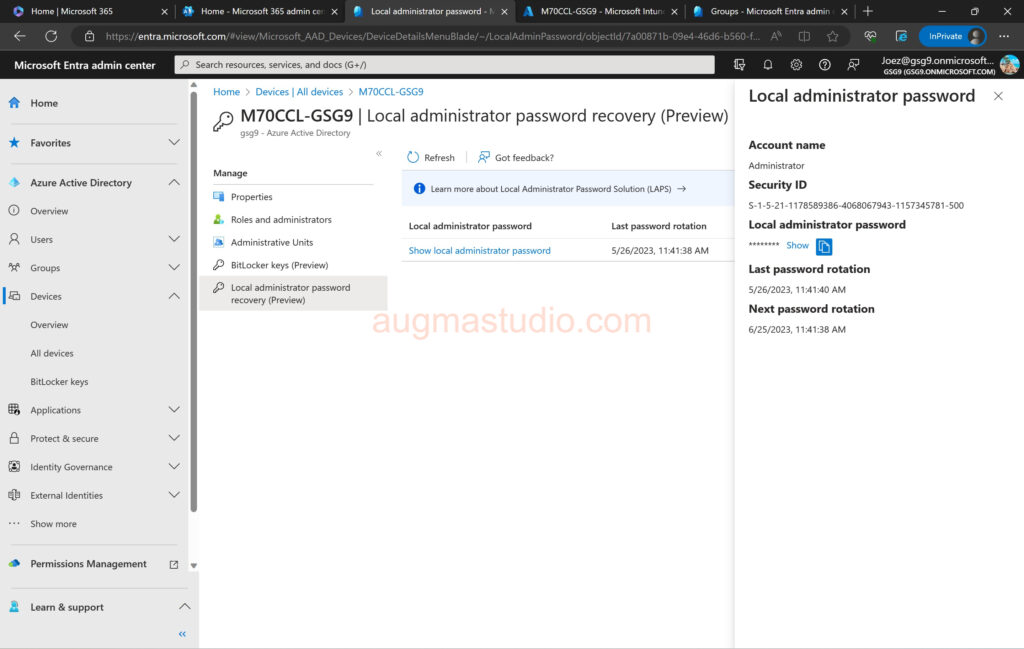
1.Login Azure Portal with your credential > Devices > All devices > Select targeted device > Local administrator password recovery (Preview) > Show local administrator password > show.
2.Or you can login to Intune admin center > Devices > All devices > select targeted device > Local admin password > Show local administrator password > show.
Additional
Windows LAPS does not support Azure Active Directory workplace-joined devices (WPJ). Devices that are joined to AzureAD can only back up passwords to AzureAD. Devices that are joined to Windows Server Active Directory can only back up passwords to Windows Server Active Directory (On-premises).
The LAPS profile (policy) that created on Intune do not create new account or password. Instead, it manage the existing local admin account on the device. If you are intend to using the default “Administrator” account, make sure its enabled and uncheck password never expired.
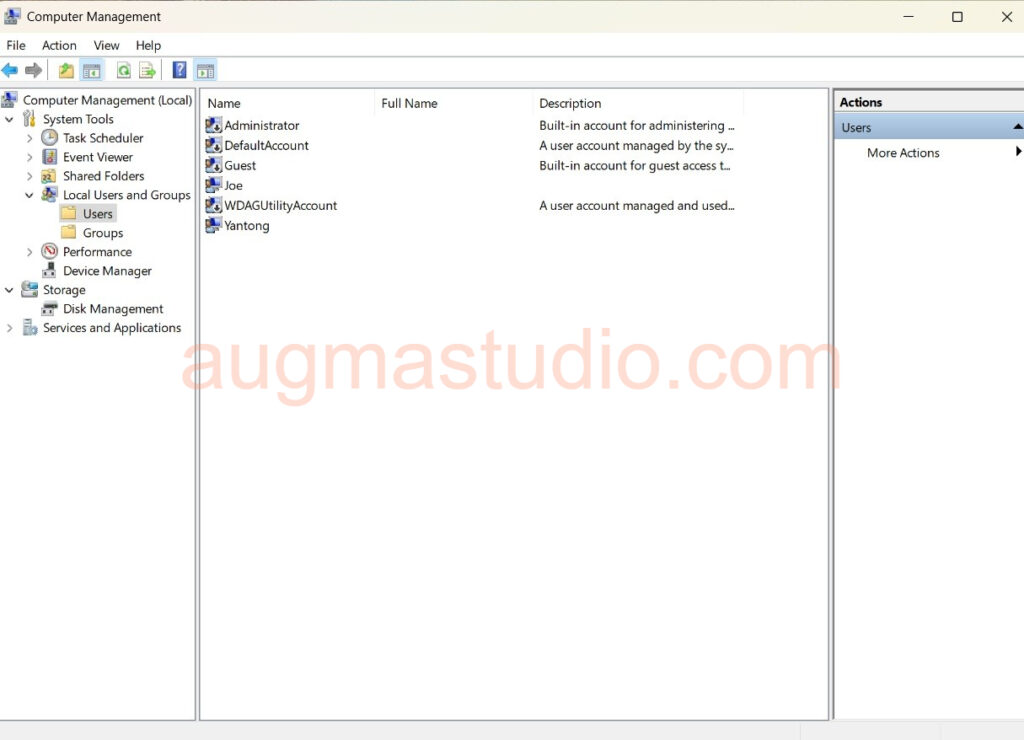
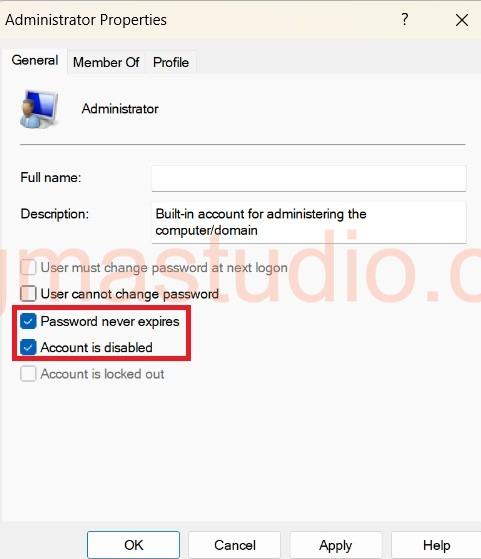
Intune profile (policy) manage LAPS by using the Windows LAPS configuration service provider (CSP). Windows LAPS CSP configuration takes precedence over, and overwrite and existing configuration from other LAPS sources, like GPOs or the Legacy LAPS.
External reference
April 11, 2023—KB5025239 (OS Build 22621.1555) – Microsoft Support
Download Local Administrator Password Solution (LAPS) from Official Microsoft Download Center
Windows LAPS frequently asked questions | Microsoft Learn
Key concepts in Windows LAPS | Microsoft Learn
Create Intune policies to configure and manage Windows LAPS | Microsoft Learn



